H3C PPP认证试验报告(h3c网上学
发布时间:2019-09-21 11:10:07编辑:auto阅读(2506)
-
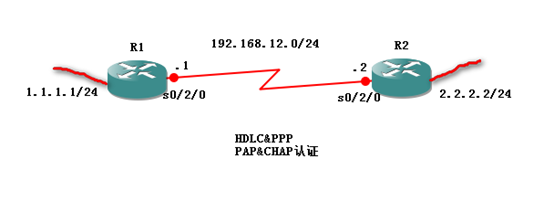
根据实验拓扑合理的规划IP,并正确的对相应的接口配置IP地址;
-
为了摸 拟PC,在两台路由器上分别启一个回环口,并进行IP地址的分配;
-
使用RIPV2实现网络互连;且关闭自动汇总功能;
-
在接口上查看默认封装的协议是HDLC还是PPP,只有PPP才支持认证;
-
配置PAP明文认证(单向认证和双向认证);
-
配置CHAP密文认证(单向认证和双向认证);
实验环境:两台H3C路由器,使用串行线缆相连;
实验目的:两台路由器之间实现PAP和CHAP认证,熟练掌握认证的配置;
实验步骤:
详细操作请见如下截图及相关文字说明:
R1的基本配置部分
[r1]dis cur
#
version 5.20, Alpha 1011
#
sysname r1
#
password-control login-attempt 3 exceed lock-time 120
#
undo voice vlan mac-address 00e0-bb00-0000
#
ipsec cpu-backup enable
#
undo cryptoengine enable
#
domain default enable system
#
vlan 1
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
#
local-user rt2
service-type ppp
#
interface Serial0/2/0
link-protocol hdlc
ip address 192.168.12.1 255.255.255.0
#
interface Serial0/2/1
link-protocol ppp
#
interface Serial0/2/2
link-protocol ppp
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Ethernet0/4/0
port link-mode bridge
#
interface Ethernet0/4/1
port link-mode bridge
#
interface Ethernet0/4/2
port link-mode bridge
#
interface Ethernet0/4/3
port link-mode bridge
#
interface Ethernet0/4/4
port link-mode bridge
#
interface Ethernet0/4/5
port link-mode bridge
#
interface Ethernet0/4/6
port link-mode bridge
#
interface Ethernet0/4/7
port link-mode bridge
#
interface GigabitEthernet0/1/0
port link-mode route
#
rip 1
undo summary
version 2
network 192.168.12.0
network 1.0.0.0
#
load xml-configuration
#
user-interface con 0
user-interface vty 0 4
R2的基本配置部分
r2>
%Mar 7 16:33:02:937 2011 r2 SHELL/4/LOGIN: Console login from con0
<r2>sys
System View: return to User View with Ctrl+Z.
[r2]dis cur
#
version 5.20, Alpha 1011
#
sysname r2
#
password-control login-attempt 3 exceed lock-time 120
#
undo voice vlan mac-address 00e0-bb00-0000
#
ipsec cpu-backup enable
#
undo cryptoengine enable
#
domain default enable system
#
vlan 1
#
domain system
authentication ppp local
access-limit disable
state active
idle-cut disable
self-service-url disable
#
local-user rt1
#
interface Ethernet0/1/0
port link-mode route
#
interface Serial0/2/0
link-protocol ppp
ip address 192.168.12.2 255.255.255.0
#
interface Serial0/2/1
link-protocol ppp
#
interface Serial0/2/2
link-protocol ppp
#
interface Serial0/2/3
link-protocol ppp
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
interface Ethernet0/4/0
port link-mode bridge
#
interface Ethernet0/4/1
port link-mode bridge
#
interface Ethernet0/4/2
port link-mode bridge
#
interface Ethernet0/4/3
port link-mode bridge
#
interface Ethernet0/4/4
port link-mode bridge
#
interface Ethernet0/4/5
port link-mode bridge
#
interface Ethernet0/4/6
port link-mode bridge
#
interface Ethernet0/4/7
port link-mode bridge
#
rip 1
undo summary
version 2
network 192.168.12.0
network 2.0.0.0
#
load xml-configuration
#
user-interface con 0
user-interface vty 0 4
#
return
在R1上面可以成功的PING通R2的回环口的地址
r1]ping -a 1.1.1.1 2.2.2.2
PING 2.2.2.2: 56 data bytes, press CTRL_C to break
Request time out
Reply from 2.2.2.2: bytes=56 Sequence=2 ttl=255 time=30 ms
Reply from 2.2.2.2: bytes=56 Sequence=3 ttl=255 time=20 ms
Reply from 2.2.2.2: bytes=56 Sequence=4 ttl=255 time=1 ms
Reply from 2.2.2.2: bytes=56 Sequence=5 ttl=255 time=10 ms
--- 2.2.2.2 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 1/15/30 ms
在R2 上面查看接口默认的封装协议是PPP
在R2上面可以成功的PING通R2的回环口的地址 r2]ping -a 2.2.2.2 1.1.1.1 --- 1.1.1.1 ping statistics --- 现将R2的S0/2/0接口的封装协议改为HDLC,发现接口DOWN掉,因此可以说明两极的封装必须一致 [r2]int s0/2/0
PING 1.1.1.1: 56 data bytes, press CTRL_C to break
Reply from 1.1.1.1: bytes=56 Sequence=1 ttl=255 time=43 ms
Reply from 1.1.1.1: bytes=56 Sequence=2 ttl=255 time=10 ms
Reply from 1.1.1.1: bytes=56 Sequence=3 ttl=255 time=10 ms
Reply from 1.1.1.1: bytes=56 Sequence=4 ttl=255 time=1 ms
Reply from 1.1.1.1: bytes=56 Sequence=5 ttl=255 time=10 ms
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 1/14/43 ms
[r2-Serial0/2/0]link-pro
[r2-Serial0/2/0]link-protocol hdlc
%Mar 7 16:38:02:984 2011 r2 IFNET/4/UPDOWN:
Line protocol on the interface Serial0/2/0 is DOWN
%Mar 7 16:38:02:984 2011 r2 IFNET/4/UPDOWN:
Protocol PPP IPCP on the interface Serial0/2/0 is DOWN
[r2-Serial0/2/0]
%Mar 7 16:38:03:875 2011 r2 IFNET/4/UPDOWN:
Line protocol on the interface Serial0/2/0 is UP
上一篇: 批量管理python脚本
下一篇: [Unity3D] U3D实现与iOS交
- openvpn linux客户端使用
52235
- H3C基本命令大全
52152
- openvpn windows客户端使用
42299
- H3C IRF原理及 配置
39171
- Python exit()函数
33667
- openvpn mac客户端使用
30621
- python全系列官方中文文档
29323
- python 获取网卡实时流量
24286
- 1.常用turtle功能函数
24172
- python 获取Linux和Windows硬件信息
22542
- LangChain 1.0-Agent中间件-实现闭环(批准-编辑-拒绝动作)
126°
- LangChain 1.0-Agent中间件-汇总消息
129°
- LangChain 1.0-Agent中间件-删除消息
142°
- LangChain 1.0-Agent中间件-消息压缩
134°
- LangChain 1.0-Agent中间件-多模型动态选择
182°
- LangChain1.0-Agent-部署/上线(开发人员必备)
344°
- LangChain1.0-Agent-Spider实战(爬虫函数替代API接口)
391°
- LangChain1.0-Agent(进阶)本地模型+Playwright实现网页自动化操作
389°
- LangChain1.0-Agent记忆管理
366°
- LangChain1.0-Agent接入自定义工具与React循环
405°
- 姓名:Run
- 职业:谜
- 邮箱:383697894@qq.com
- 定位:上海 · 松江